Passwords have been a method of passage since ancient times. To be granted access to a location or resource, an employee is required to utter or type the correct secret phrase. In military terminology, in addition to a password, a counter password exists as an additional secret and challenge (besides the main password) that aids in the recognition of enemy subjects.
In information technology, the use of passwords as a means of authentication in access systems is both widespread and a widely discussed topic due to the deteriorating level of security. In security and authentication systems, passwords are stored in databases forming pairs of username and secret records. In order to achieve a good level of security and lower the risk of unintentional or intentional disclosure of passwords, a variety of cryptographic methods are used to store the password in encrypted form.
Naturally, even if passwords are stored in encrypted form using block encryption or one-way hashing, they are not secure. The main characteristic of passwords is their complexity, dividing passwords into two types: strong and weak passwords that can be subjectively evaluated.
Types of passwords
Weak passwords are those that use a small number of characters, as well as the same type of characters, such as only letters, only numbers, or simple (short) words. Example of a weak password: 123456789, password, qwerty, love, etc.
Strong passwords are those that contain a large number of characters (at least 12) and use a combination of letters, numbers and special characters and/or phrases. Examples of a strong password: “Trial Parent Book Demand 5”, “AX3ThM2q@23devGuxzPcqN2d9JssRc-K”
Password and secret cracking attacks
- Brute force. To find the correct password, an attacker tries to crack the password using all possible combinations. The time to crack a password depends directly on its complexity and the number of attempts that can be made per unit time. Examples can be found in the table below as it is only indicative, as the actual results depend on both the complexity and length of the password and the computational resource used to crack the password. The trends are for the red zone to gradually grow and take over adjacent cells, i.e. cracking complex passwords to become faster and easier over time.
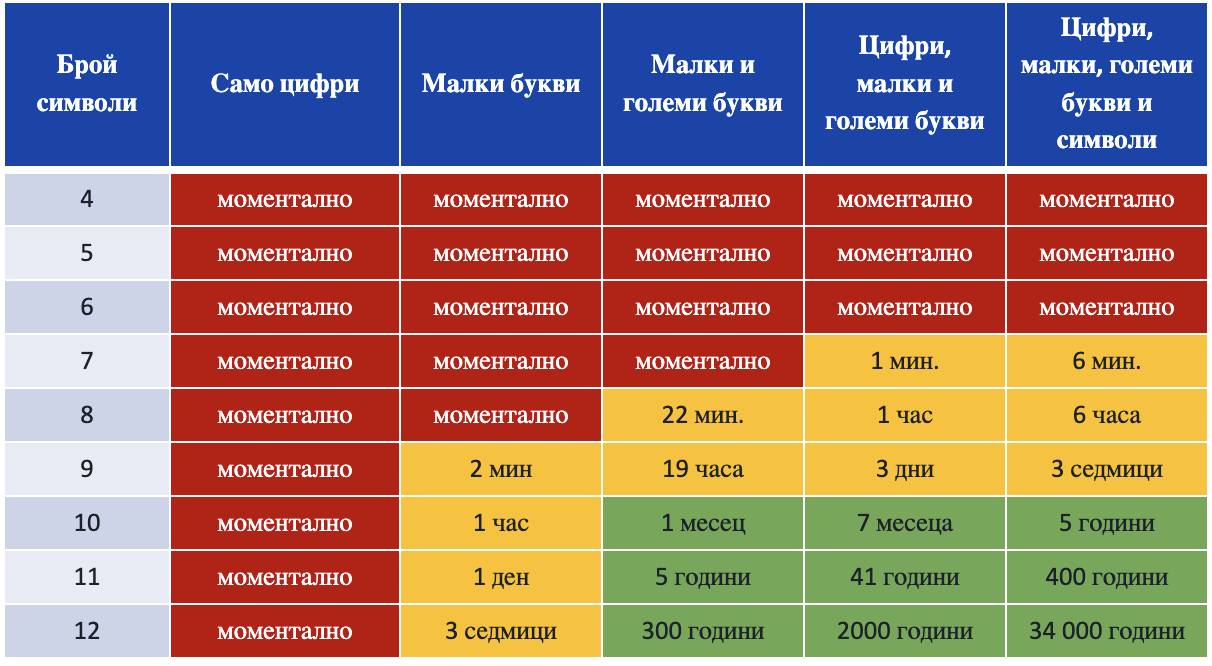
- Dictionary attack – this attack is very similar to brute force, but it uses ready-made dictionaries with redefined words, phrases and commonly used passwords or passwords from already cracked databases (of products and services).
- Mask attack – this technique resembles a dictionary attack, but for this purpose, clear personal information about the victim is used in advance and the clear assumption is made that the password contains names and elements with sentimental value and/or names from the victim’s personal environment (names of loved ones, phone numbers, address, hometown, hobby, etc.).
- Rainbow table attack – this type of attack is launched if the attacker has access to or has already compromised a table with passwords that are “hashed”, i.e. has the “hash” of the password. The hash is a one-way generation of a string of random characters using the original password as the key. In this way, it is not the passwords that are stored in the database, but the result of the hashing operation, which is one-way without the possibility of backward replay. For the attack, pre-generated hash and key pair tables are used by searching for an equivalent hash and its key that can be used.
- Man in the middle attack – This type of attack is typical when using public Internet access networks where the victim is connected and using a compromised network. In this way, all traffic is intercepted, and with it any secrets, keys, usernames that may have been transmitted over an insecure channel or the connection was encrypted using insecure algorithms or weak keys.
Social engineering attacks:
-
- Phishing attack – a spoofed or compromised email from a reputable institution is used, inviting the victim to open an external link and enter personal information (usernames, passwords, credit cards, name, addresses, etc.).
- Surveillance (Shoulder surfing) – used to directly or indirectly (through cameras or tracking devices) monitor the victim as they enter their username and password.
- Direct manipulation through interview and cold reading. Through a series of misleading and manipulative questions, circumstances are created in which the victim uncontrollably begins to provide information and artifacts about parts of the password, and sometimes the entire password.
How to protect ourselves?
There is no one-size-fits-all rule that will protect us from absolutely all password-related threats, and also we as end users have no control over the technical design and construction of the password authentication and storage mechanism, so we need to use a combination of various small and easy-to-implement techniques that reduce the chance of password cracking.
The main tips are:
- Always use a complex password preferably over 18 characters
- Change passwords frequently (at least once every 6 months), and for critical services, even more frequently
- It is mandatory to use multi-factor authentication: email code, sms code, OTP services (one time password), USB security stick and combinations related to them.
- Password wallets – service products like KeePass & 1Password that help in generating and storing strong passwords.
- Never use the same password for multiple services.
- Being private and keeping passwords and PINs away from prying eyes
- Use only secure and designated communication devices, channels and environments
- Do not use public and unsecured networks for communication
- Check emails and messages for signs of malicious intent before taking further steps
- Avoid feelings of untouchability, impenetrability and perfectionism. There is always a first time.
